Pivolt - AI-Powered Investment Solutions
Infrastructure
Pivolt is a SaaS platform designed for Investment Management, built on four core pillars: experience, technology, productivity, and excellence. Our systems are hosted in a secure, firewall-protected environment, ensuring prevention against interference or unauthorized access.

Infrastructure - Azure
Hosted on Microsoft Azure, Pivolt leverages enterprise-grade security to restrict access, segregate responsibilities, and provide detailed logs for auditing and monitoring customer assets. Fault-tolerant data centers enable high-availability and attack-resilient architectures, supported by third-party audited security frameworks.
Security - Pivolt
Comprehensive security measures including strong password policies, advanced authentication protocols, and software-as-a-service protection.


Security - Database
Access to production databases is tightly controlled, restricted to limited points, and protected by unique credentials to ensure operational integrity.

Security SSL
Pivolt employs SSL Digital Certificates to encrypt sensitive data, ensuring that all transmitted information, such as usernames and passwords, is secure. This prevents interception and guarantees decryption only by the authorized server.

Security - Server IP
Comprehensive server IP scans perform over 11,000 vulnerability tests across a wide range of applications and operating systems, ensuring robust security protocols.
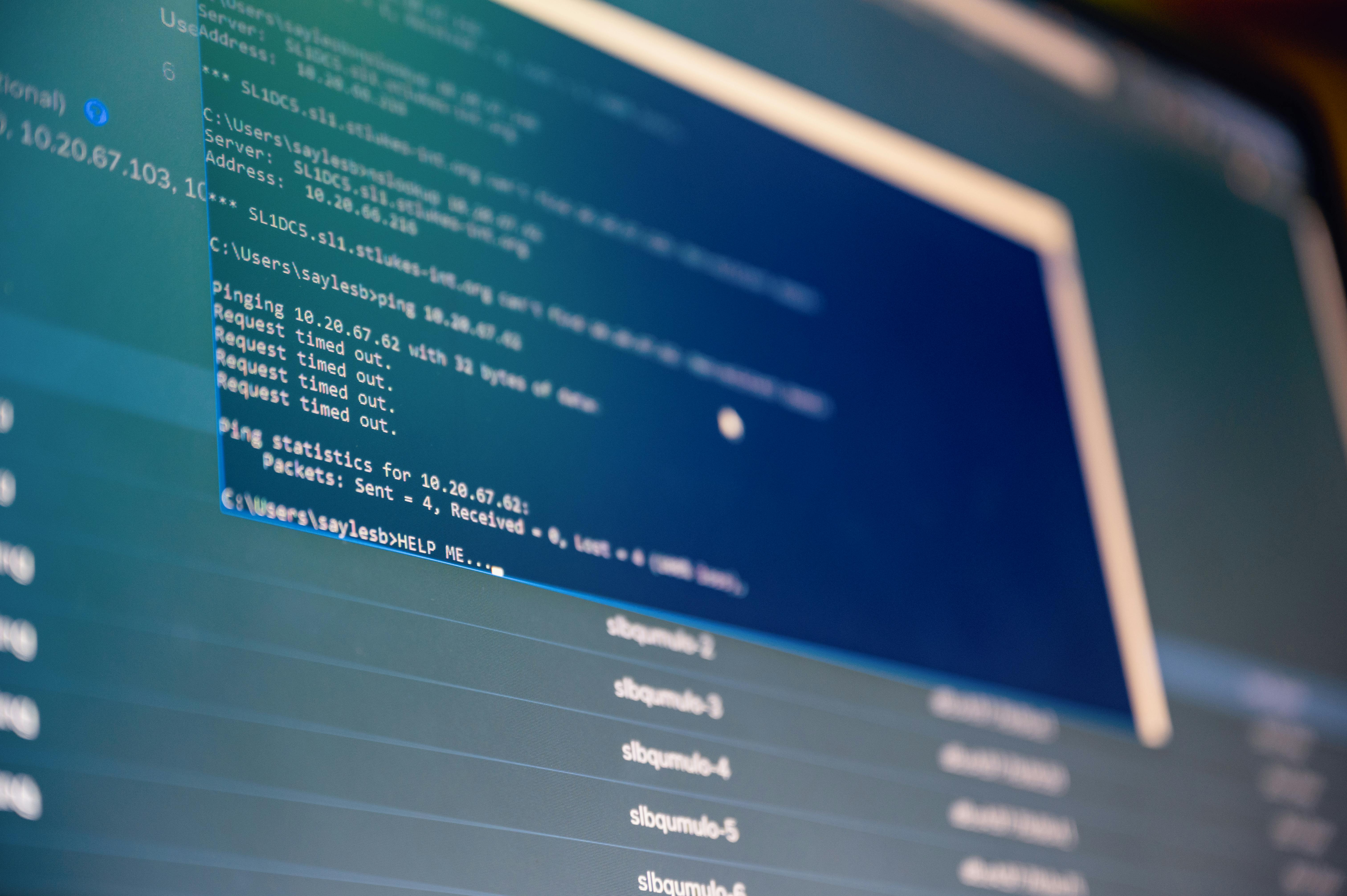
Security - PenTest
Penetration Testing identifies vulnerabilities often missed by automated tools. Pivolt’s security team evaluates adherence to seven critical security points, uncovering potential failures to strengthen web application defenses.

Backup Policy
Comprehensive backup policies include secure storage locations, frequent database backups, and robust recovery plans to safeguard client data.

